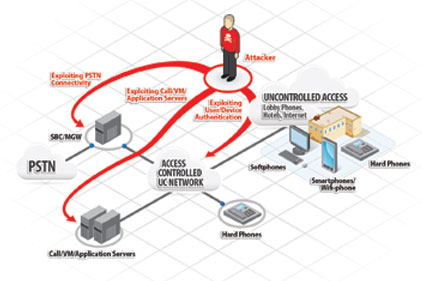
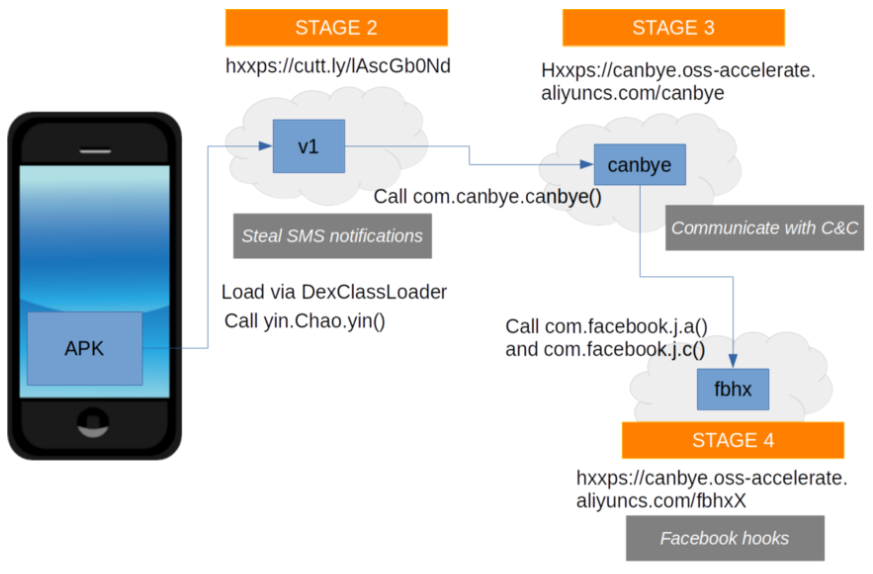
Discovering the phone phreaks, the original hackers who unraveled telephone secrets, shaping the cybersecurity landscape. 🌐🕵️�... | Instagram

Exploding the Phone: The Untold Story of the Teenagers and Outlaws who Hacked Ma Bell by Phil Lapsley | Goodreads