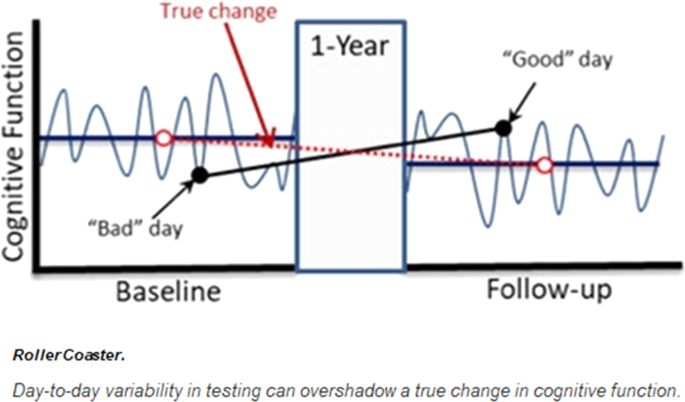
Frontiers | SSVEP BCI and Eye Tracking Use by Individuals With Late-Stage ALS and Visual Impairments
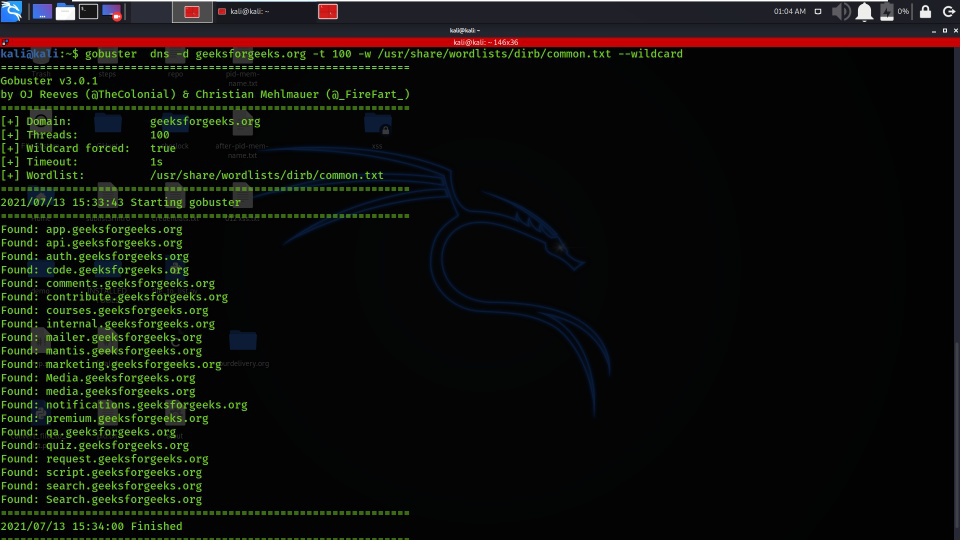
GitHub - jimywork/shodanwave: Shodanwave is a tool for exploring and obtaining information from Netwave IP Camera.

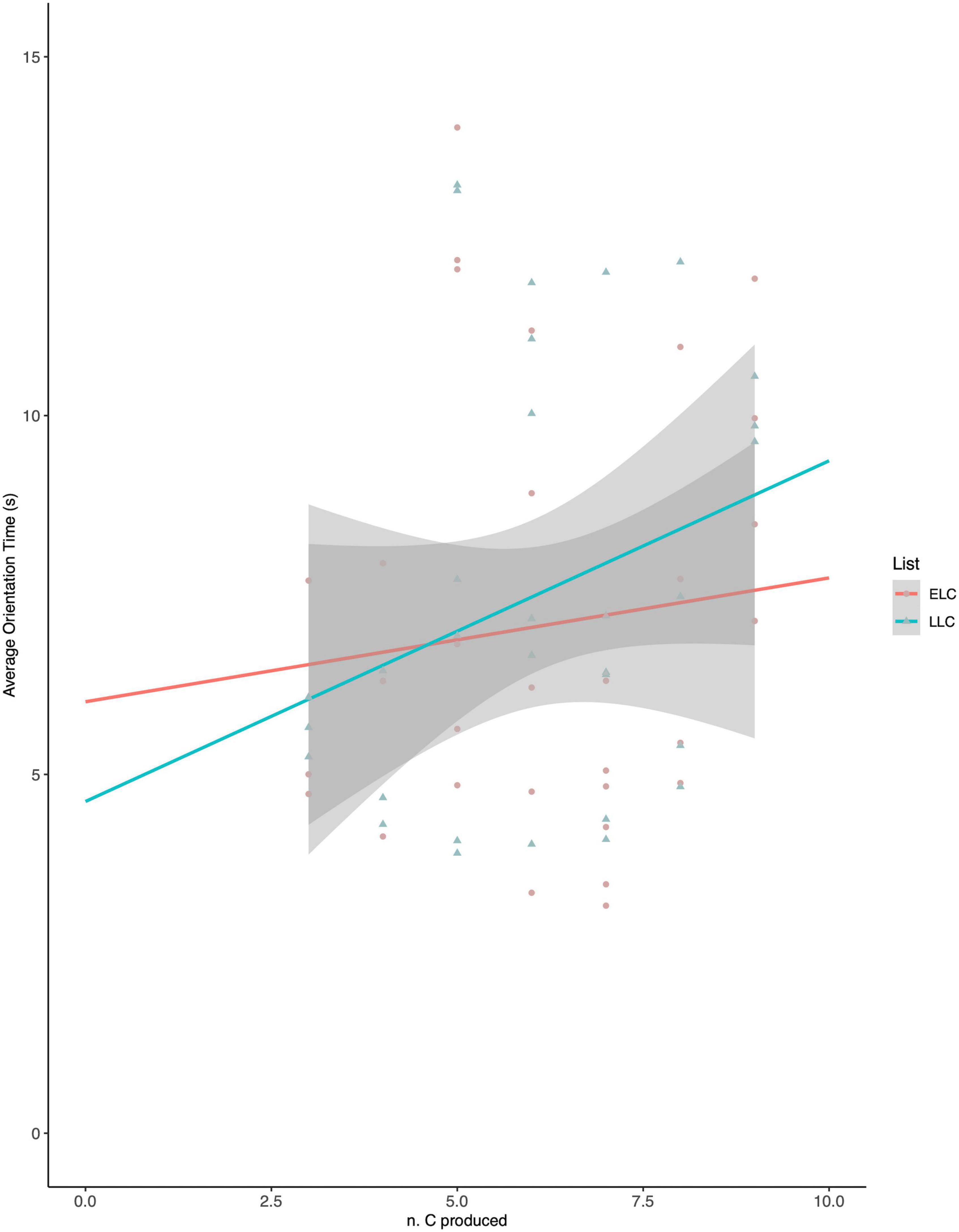
Stimulating learner engagement in app-based L2 vocabulary self-study: Goals and feedback for effective L2 pedagogy - ScienceDirect

Maximising security and compliance features from Microsoft 365 E5 license - 22 November 2022 | Local Government Association

J. Imaging | Free Full-Text | Empowering Deaf-Hearing Communication: Exploring Synergies between Predictive and Generative AI-Based Strategies towards (Portuguese) Sign Language Interpretation

GigE Vision® Device IP Package (1GbE version/10GbE version) (Discontinued) - Semiconductor Business -Macnica,Inc.
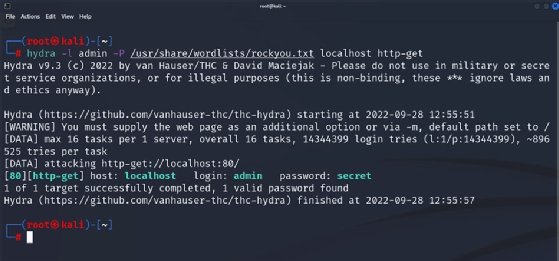
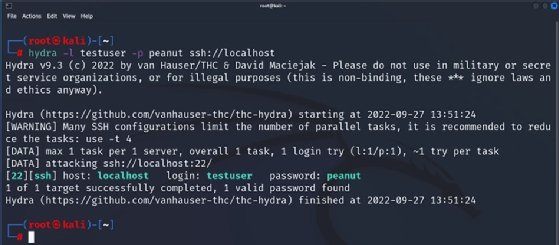
GitHub - prosecurity/wordlist-1: Collection of some common wordlists such as RDP password, user name list, ssh password wordlist for brute force. IP Cameras Default Passwords.

Applied Sciences | Free Full-Text | Design of OCC Indoor Positioning System Based on Flat Panel Light and Angle Sensor Assistance
GitHub - vlepilov/wordlist-1: Collection of some common wordlists such as RDP password, user name list, ssh password wordlist for brute force. IP Cameras Default Passwords.